Proxy: Definition, Working Mechanism, Benefits, and Real-life Examples
A proxy is a server or a computer system that acts as an intermediary between a client and a target server. It acts as a gateway, forwarding requests from the client to the target server and returning the response back to the client. The main purpose of using a proxy is to provide anonymity and improve performance by caching and filtering requests.
Working Mechanism
When a client makes a request to access a website or any online resource, it first connects to the proxy server instead of directly connecting to the target server. The proxy server then evaluates the request and forwards it to the target server on behalf of the client. The target server processes the request and sends the response back to the proxy server, which in turn sends it back to the client.
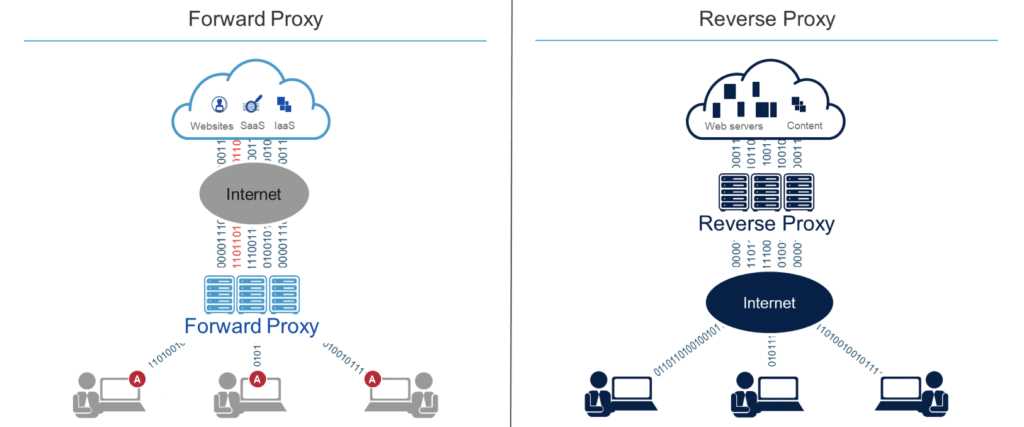
Proxies can be configured to work in different ways, such as:
Benefits of Using Proxies
Using proxies offers several benefits, including:
- Anonymity: Proxies can hide the client’s IP address, making it difficult for websites to track their online activities.
- Improved Performance: Proxies can cache frequently accessed resources, reducing the load on the target server and improving response times.
- Access Control: Proxies can be configured to restrict access to certain websites or resources, providing control over internet usage.
- Security: Proxies can act as a barrier between the client and the target server, protecting the client from malicious websites and attacks.
Real-life Examples of Proxy Usage
Proxies are widely used in various industries and scenarios, including:
- Corporate Networks: Companies use proxies to control and monitor internet access, enforce security policies, and improve performance.
- Web Scraping: Proxies are used in web scraping to gather data from websites without being blocked or detected.
- Geo-blocking Bypass: Proxies can be used to bypass geo-blocking restrictions and access region-restricted content.
- Anonymous Browsing: Proxies can provide anonymity to users who want to browse the internet without revealing their identity.
A proxy is a server or a computer system that acts as an intermediary between a client device and the internet. It acts as a gateway, forwarding requests from the client to the target server and returning the responses back to the client. The use of a proxy allows users to access the internet indirectly, providing various benefits and functionalities.
Proxies work by intercepting the client’s request and forwarding it to the target server on behalf of the client. The target server sees the request as coming from the proxy server rather than the client device. This helps to hide the client’s IP address and location, providing anonymity and privacy.
Benefits of Using Proxies
Using a proxy server offers several benefits:
- Anonymity: Proxies help to hide the client’s IP address and location, making it difficult for websites and online services to track their online activities.
- Access Control: Proxies can be used to restrict or grant access to specific websites or online services. This is commonly used in corporate environments to control employee internet usage.
- Content Filtering: Proxies can be configured to filter out unwanted content, such as advertisements, malicious websites, or inappropriate content. This helps to improve internet browsing experience and security.
- Improved Performance: Proxies can cache frequently accessed web pages, reducing the load on the target server and improving overall performance.
- Geo-blocking Bypass: Proxies can be used to bypass geo-blocking restrictions, allowing users to access content that is restricted to specific geographic regions.
Real-life Examples of Proxy Usage
Proxies are widely used in various industries and scenarios:
- Corporate Networks: Companies use proxies to control internet access, protect sensitive data, and improve network performance.
- Web Scraping: Proxies are commonly used in web scraping to gather data from websites without being blocked or detected.
- Online Advertising: Advertisers use proxies to test and monitor their campaigns, ensuring accurate targeting and preventing fraud.
- Content Localization: Proxies are used to provide localized content to users based on their geographic location.
- Security and Privacy: Proxies can be used to enhance security and privacy by encrypting internet traffic and hiding the user’s identity.
How Proxies Work
A proxy acts as an intermediary between a user and the internet. When a user requests a web page or any other online resource, the request is first sent to the proxy server. The proxy server then forwards the request to the destination server on behalf of the user. The destination server sends the response back to the proxy server, which in turn sends it back to the user.
Proxies work by intercepting and handling network traffic between the user and the internet. They can be set up on a local network or accessed remotely. There are different types of proxies, including HTTP proxies, SOCKS proxies, and VPNs, each with its own specific functionality and use cases.
Proxy Server
A proxy server is a computer or a software application that acts as an intermediary between a user and the internet. It receives requests from users and forwards them to the destination server. The proxy server can also cache web pages and other resources, allowing for faster access and reducing bandwidth usage.
Proxy servers can be used for various purposes, such as improving security and privacy, bypassing content restrictions, and optimizing network performance. They can be set up on a local network or accessed remotely through a proxy service provider.
Proxy Types
There are different types of proxies, each with its own functionality and use cases:
- HTTP Proxies: These proxies are designed to handle HTTP traffic and are commonly used for web browsing. They can filter and modify web content, block certain websites, and provide anonymity by hiding the user’s IP address.
- SOCKS Proxies: SOCKS (Socket Secure) proxies can handle various types of network traffic, including HTTP, FTP, and SMTP. They are commonly used for applications that require more advanced networking capabilities, such as torrenting or accessing restricted networks.
- VPN (Virtual Private Network): A VPN is a type of proxy that creates a secure and encrypted connection between a user and the internet. It can be used to bypass censorship, protect privacy, and access geographically restricted content.
Proxies can be set up on individual devices, such as computers or smartphones, or on a network level, where all devices on the network route their traffic through the proxy server.
Overall, proxies play a crucial role in enhancing security, privacy, and performance for users accessing the internet. They provide a layer of abstraction between the user and the internet, allowing for more control and flexibility in managing online activities.
Benefits of Using Proxies
Proxies offer a wide range of benefits for individuals and businesses alike. Here are some of the key advantages of using proxies:
1. Enhanced Privacy and Security: One of the main benefits of using proxies is the increased privacy and security they provide. Proxies act as intermediaries between your device and the internet, masking your IP address and encrypting your online activities. This helps protect your sensitive information from hackers, identity thieves, and other malicious actors.
2. Access to Blocked Content: Proxies can be used to bypass geographical restrictions and access blocked content. By connecting to a proxy server located in a different country, you can appear as if you are browsing from that location. This is particularly useful for individuals who want to access region-restricted websites, streaming services, or social media platforms.
3. Improved Performance: Proxies can also improve your internet browsing experience by caching web content. When you request a webpage, the proxy server stores a copy of the content. If you or someone else requests the same webpage again, the proxy server can deliver the cached version instead of retrieving it from the original source. This can significantly reduce load times and improve overall performance.
4. Load Balancing: Proxies can distribute network traffic across multiple servers, helping to balance the load and prevent server overload. This is particularly beneficial for businesses with high website traffic or online services that require consistent performance. By distributing the workload, proxies can ensure that each server operates efficiently and effectively.
5. Anonymity: Proxies allow users to maintain anonymity while browsing the internet. By masking your IP address and routing your internet traffic through a proxy server, you can browse websites without revealing your true identity. This can be useful for individuals who wish to protect their privacy, avoid targeted advertising, or bypass censorship.
6. Web Scraping and Data Gathering: Proxies are commonly used for web scraping and data gathering purposes. With the help of proxies, you can send multiple requests to a website without getting blocked or banned. By rotating IP addresses and distributing requests across different proxies, you can collect large amounts of data without triggering any restrictions.
Real-life Examples of Proxy Usage
Proxies are widely used in various real-life scenarios to enhance privacy, security, and access to information. Here are some examples of how proxies are utilized:
1. Web Scraping: Proxy servers are commonly used in web scraping, where automated bots extract data from websites. By using proxies, web scrapers can rotate their IP addresses and avoid getting blocked by websites that have anti-scraping measures in place.
2. Geo-blocking Bypass: Proxies can be used to bypass geo-blocking restrictions imposed by websites and streaming platforms. For example, if a user wants to access content that is only available in a specific country, they can use a proxy server located in that country to appear as if they are accessing the content from within the country.
3. Anonymity and Privacy: Proxies are often used to maintain anonymity and privacy while browsing the internet. By routing their internet traffic through a proxy server, users can hide their real IP address and location, making it difficult for websites and online services to track their activities.
4. Load Balancing: Proxies are used in load balancing scenarios to distribute network traffic across multiple servers. This helps to optimize server performance and ensure that no single server becomes overloaded with requests.
5. Content Filtering: Proxies are commonly used in organizations and schools to implement content filtering policies. By routing internet traffic through a proxy server, administrators can block access to certain websites or categories of websites, ensuring that users comply with acceptable use policies.
6. Access to Restricted Content: Proxies can be used to access content that is blocked or restricted in certain regions. For example, individuals living in countries with strict internet censorship can use proxies to bypass these restrictions and access blocked websites and services.
7. Security Testing: Proxies are often used in security testing and penetration testing to simulate attacks and assess the vulnerabilities of a network or system. By routing traffic through a proxy server, testers can analyze and intercept network traffic, identify potential security flaws, and strengthen the overall security of the system.
8. Performance Optimization: Proxies can be used to optimize network performance by caching frequently accessed content. By storing copies of web pages and resources on a proxy server, subsequent requests for the same content can be served faster, reducing bandwidth usage and improving overall browsing speed.
These are just a few examples of how proxies are used in real-life scenarios. The versatility and flexibility of proxies make them an essential tool for various purposes, ranging from privacy and security to performance optimization and access to restricted content.

Emily Bibb simplifies finance through bestselling books and articles, bridging complex concepts for everyday understanding. Engaging audiences via social media, she shares insights for financial success. Active in seminars and philanthropy, Bibb aims to create a more financially informed society, driven by her passion for empowering others.
